Part 1. Synchronising your secrets to the cloud.
I have always been a fan of Postman, finding it an indispensable tool for API development and testing. However, recent updates have introduced a significant change that has left many users, including myself, feeling a bit concerned. Postman, a tool long celebrated for its accessibility and ease of use, has started nudging users towards embracing their cloud environment. This shift became particularly noticeable after a recent upgrade. Suddenly, I found myself confronted with a requirement to sign in, even for accessing basic features like environments and collections.
Notice this statement in the top: “You are using the Lightweight API Client, sign in or create an account to work with collections, environments and unlock all free features in Postman“.
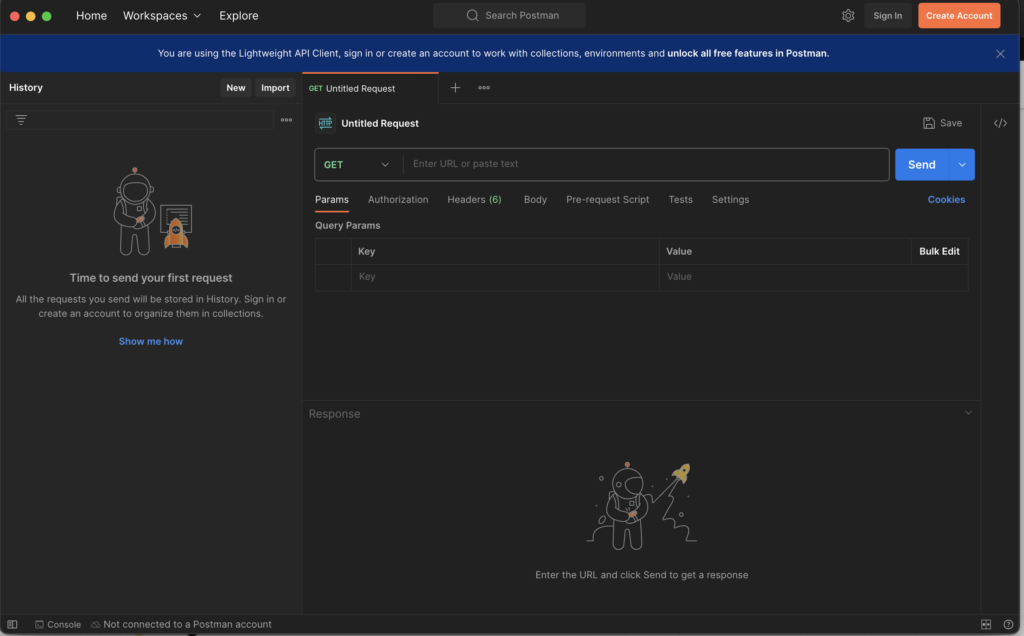
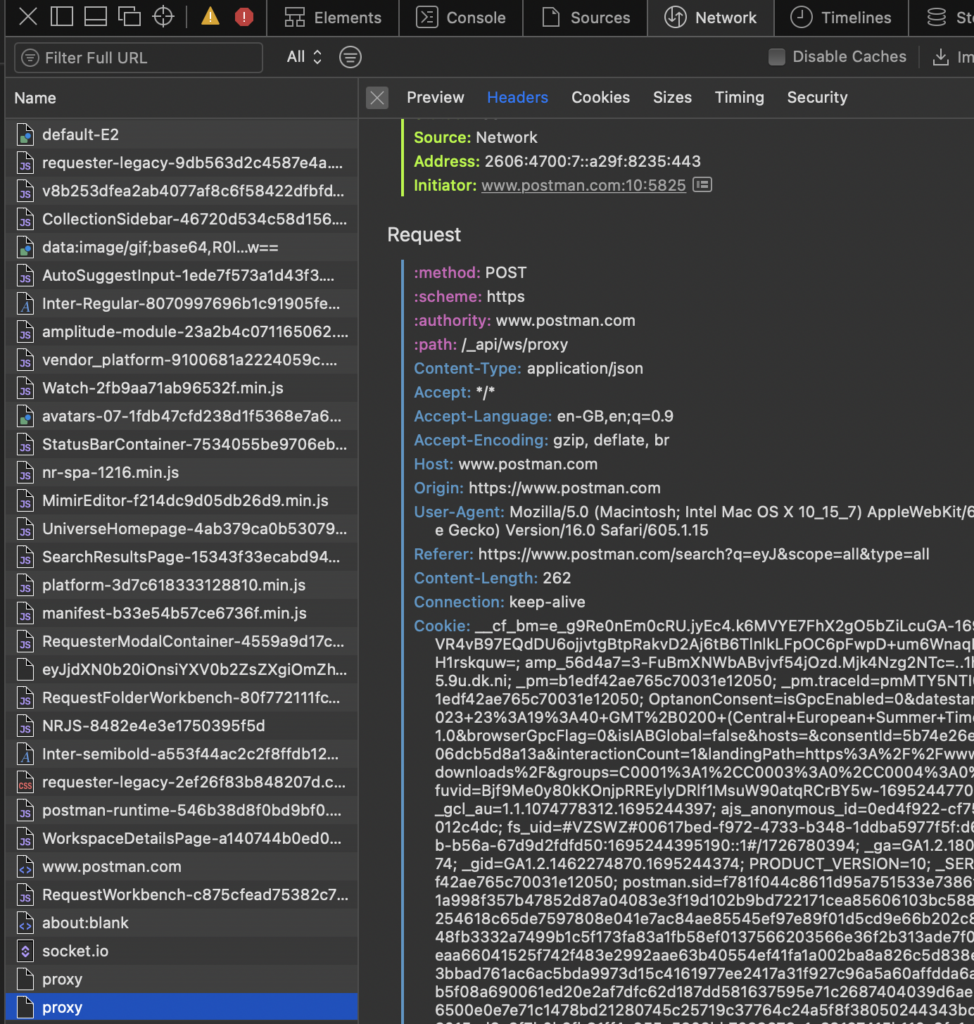
And of course, as soon as you sign in and log into the desktop tool, all your data is automagically transferred to the cloud. While cloud synchronization offers the convenience of accessing your data from anywhere, at any time, it does pose potential security and privacy concerns. Your API collections, environments(with some minor restrictions), request history(not including responses by default), and other crucial data hosted now in the cloud environment. The issue is especially noticeable upon checking the history of the requests and inspecting headers that may contain cookies, tokens and secrets that you used before:
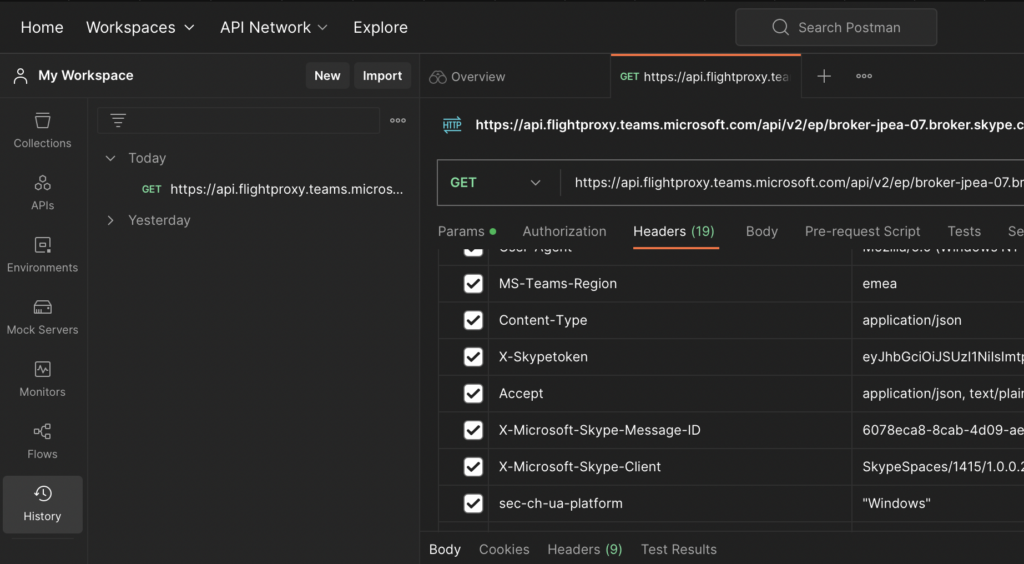
This shift raises pertinent questions regarding the security measures employed to protect this data and how much control users have over their information once it’s stored in the cloud. Unfortunately, even after reaching out for clarification, it seems that the company is trying to avoid addressing direct questions regarding this issue. In contrast Postman kindly provided a dedicated page called “Security and Trust Portal” which actually looks solid and may bring some basic trust. Bug given that almost all web-developers use this tool on a daily basis to access (often production) environments should they trust enough to allow it to keep all the secrets in the cloud? If we consider the increasing number of security breaches happening these days across major cloud providers such as AWS and Azure, I would lean towards saying no.
So I opened a request for the security team to answer this and while waiting for the reply I played a bit with the cloud version(of course using separate non-corporate account), and would like to share yet another trivial observation that also surprised me perhaps even more…
Part 2. Postman Dorks.
The Postman web version allows you to create environments and collections that you can share with the entire network. Quite a convenient feature for the api developers. And one of the coolest features delivered is the ability to search over such public collections. But where does this lead? Something I would call ‘Postman Dorks,‘ an analogue of the well-known ‘Google Dorks‘. Essentially, these shared environments and collections, innocently intended for collaboration and efficiency, may inadvertently become a treasure trove for attackers seeking potential vulnerabilities.
Let’s try it out.
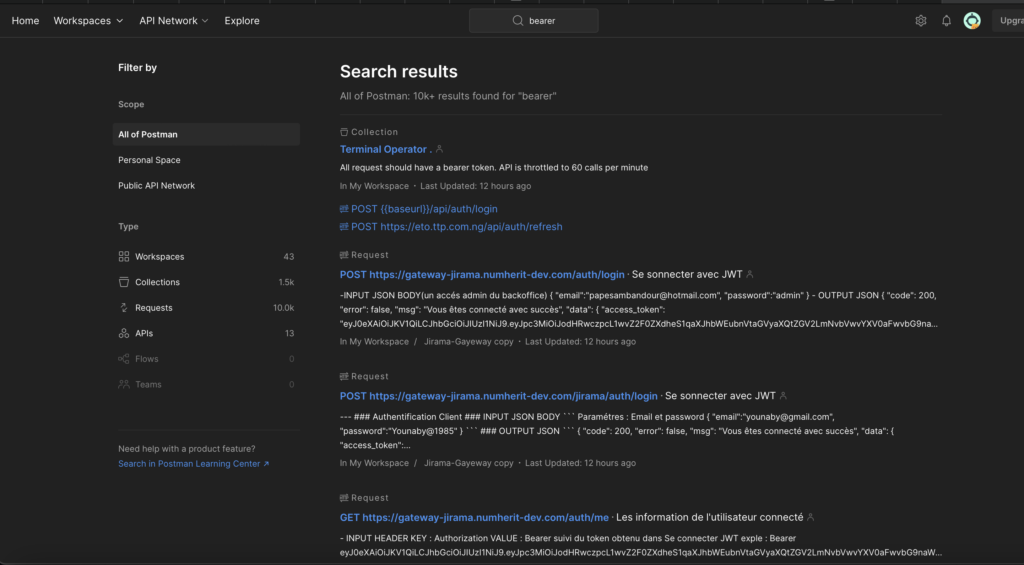
Searching for the “Bearer” key word there are about 10k+ requests, some of which contain actual tokens:
Or even better query “eyJ” for searching for JWT tokens:
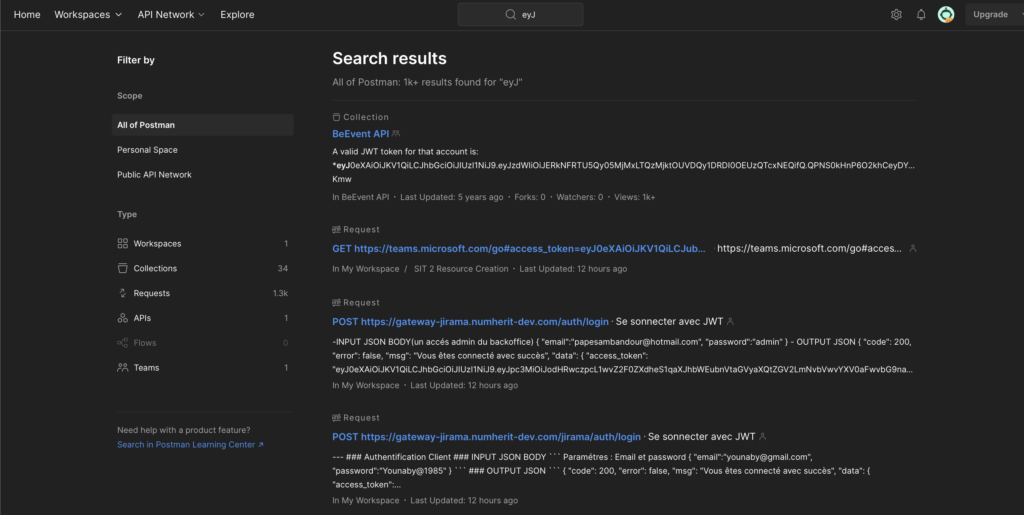
Naturally, I assume that the majority of these matches do not expose actual tokens and do not grant unauthorised access to the sensitive data. However, even if just one percent of the search results does provide unauthorised access due to a human mistake, I believe this functionality poses a significant risk because impact is huge.
And finally let’s not overlook the automation: while examining the traffic to the search API, I noticed that the requests and responses data are quite straightforward. Consequently, automating the process to collect and verify leaked secrets via Postman Cloud becomes a routine task for an experiencing developer.
Part 3. Final Conclusions
I appreciate Postman and understand the rationale behind their transformation. However, I have concerns that this specific change may compel many companies to discontinue its use due to security considerations. Having said that, I would greatly appreciate if they simply introduced a paid desktop version that does not sync my data. This way, users could maintain control over their sensitive information while still benefiting from the tool’s features and capabilities…